Peer To Peer Network Security
From Computing and Software Wiki
(New page: This is the page about P2P network security) |
|||
| (18 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | This is the | + | '''Peer-to-Peer''' (or '''P2P''') networking is a fairly popular networking concept. Networks software such as BitTorrent and eMule make it easy for people to find what they want and share what they have. The first idea for using P2P networks are to exchange pirated audio, video, software, and other inappropriate content. An important thing should be noticed that share thing files on your computer with anonymous and unknown users on the public Internet could be dangerous and lead to security problem. [4,5] |
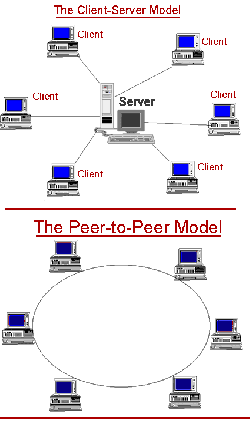
| + | [[Image:Peer_to_peer.gif|thumb|250px|right| The different between Client-Server and P2P model.[1]]] | ||
| + | |||
| + | __TOC__ | ||
| + | |||
| + | ==What is Peer to Peer Network== | ||
| + | A pure peer-to-peer network does not have the notion of clients or servers, but only equal peer nodes that simultaneously function as both "clients" and "servers" to the other nodes on the network. An example for a non P2P file transfer is an FTP server where the client and server programs are quite distinct. P2P networks are generally simpler but they usually do not offer the same performance under heavy loads. The P2P network itself relies on computing power at the ends of a connection rather than from within the network itself. Besides file sharing, P2P networks are also used for Distributed Computation or Instant messaging. [2,7] | ||
| + | |||
| + | |||
| + | ==Network Structure== | ||
| + | Peer-to-peer file sharing networks are transient Internet networks that allow computer users within the same P2P networking program to connect with each other computers and use sophisticated searching techniques to directly access and download files from one another's hard drives. The P2P overlay network consists of all the participating peers as network nodes. There are links between any two nodes that know each other. Based on how nodes link to each other, P2P networks can classify as '''Unstructured''' and '''Structured'''. [6,2] | ||
| + | |||
| + | |||
| + | ===Unstructured P2P networks=== | ||
| + | An unstructured P2P network is formed when the overlay links are established arbitrarily. Such networks can be easily constructed as a new peer that wants to join the network can copy existing links of another node and then form its own links over time. In an unstructured P2P network, if a peer wants to find a desired piece of data in the network, the query has to be flooded through the network to find as many peers as possible that share the data. The main disadvantage with such networks is that the queries may not always be resolved. Popular content is likely to be available at several peers and any peer searching for it is likely to find the same thing, but if a peer is looking for rare data shared by only a few other peers, then it is highly unlikely that search will be successful. [2] | ||
| + | |||
| + | |||
| + | ===Structured P2P networks=== | ||
| + | Structured P2P network employ a globally consistent protocol to ensure that any node can efficiently route a search to some peer that has the desired file, even if the file is extremely rare. Such a guarantee necessitates a more structured pattern of overlay links. By far the most common type of structured P2P network is the distributed hash table (DHT), in which a variant of consistent hashing is used to assign ownership of each file to a particular peer, in a way analogous to a traditional hash table's assignment of each key to a particular array slot. [2] | ||
| + | |||
| + | |||
| + | ==Security Concern== | ||
| + | One major concern of using P2P architecture in the workplace is, of course, network security. Security concerns stem from the architecture itself. Today we find most blocking and routing handles by a specific server within network, but the P2P architecture has no single fixed server responsible for routing and requests. There are many kind of P2P networking attacks that cause the security problem and we have some example below. On the other hand, most of the security mechanisms using today are based on secret key, public key or combination of them. below has some introduction of the basic aspects of them. [7,1] | ||
| + | |||
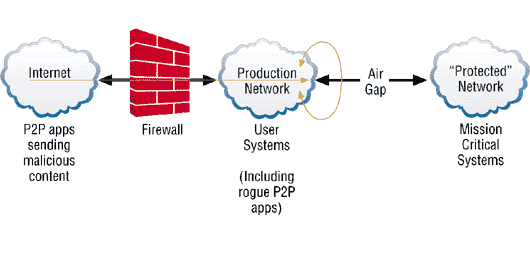
| + | The picture below shows the weakness of security when using P2P applications. It shows that these applications are allow to go though the network and the network is now not secure. [1] | ||
| + | |||
| + | [[Image:Security.gif]] | ||
| + | |||
| + | |||
| + | ===Attacks=== | ||
| + | <ul> | ||
| + | *'''TCP port''' - To share files on the computer within a P2P network such as BitTorrent, a specific TCP port must be opened for the P2P software to communicate. In effect, once you open the port you are no longer protected from malicious traffic coming through it. [4] | ||
| + | |||
| + | *'''Trojans, Viruses''' - When files are downloading from other peer, there are no guarantee that the files being transfered are the one that you want. Also, when you double-click the EXE file, you can not sure that it has not installed a Trojans or bring viruses to the computer. [4] | ||
| + | |||
| + | *'''Malware''' - The P2P network software itself may contain [http://en.wikipedia.org/wiki/Malware malware] or [http://en.wikipedia.org/wiki/Spyware spyware]. [2] | ||
| + | |||
| + | *'''Bandwidth Clogging and File Sharing''' - P2P applications such as BitTorrent make it possible for one computer to share files with another computer located somewhere else on the Internet. A major problem with P2P file-sharing programs is that they result in heavy traffic, which clogs the institution networks. The rich audio and video files that P2P users share are very big. This affects response times for internal users as well as e-business customers and that results in lost income. [1] | ||
| + | </ul> | ||
| + | |||
| + | |||
| + | ===Security Mechanisms=== | ||
| + | <ul> | ||
| + | *'''Secret Key''' - Secret key techniques are based on the fact that the sender and recipient share a secret, which is used for various cryptographic operations, such as encryption and decryption of messages and the creation and verification of message authentication data. This secret key must be exchanged in a separate out of bound procedure prior to the intended communication (using a PKI for example). [1] | ||
| + | |||
| + | *'''Public Key''' - Public Key Techniques are based on the use of asymmetric key pairs. Usually each user is in possession of just one key pair. One of the pair is made publicly available, while the other is kept private. Because one is available there is no need for an out of band key exchange, however there is a need for an infrastructure to distribute the public key authentically. Because there is no need for pre-shared secrets prior to a communication, public key techniques are ideal for supporting security between previously unknown parties. [1] | ||
| + | |||
| + | *'''Trust''' - Trust is necessary in any distributed application -- P2P applications included. Trust can become a serious issue for P2P applications that distribute processing work to distributed computing nodes and then collect the results. If you trust a node within the network, you might be tempted to trust the content it provides. In some cases, this assumption is reasonable, but not always. '''Trust''' can established by these three standard elements. [3] | ||
| + | |||
| + | <ul> | ||
| + | *'''Authentication''' - This process determine which node is in fact who or what that node declares itself to be. [3] | ||
| + | |||
| + | *'''Authorization''' - It gives an authentication to other node to access some subset of the resource s on another peer. [3] | ||
| + | |||
| + | *'''Encryption''' - This process coverts understandable information (plaintext) into a form difficult to understand by unauthorized individuals and systems. One use of encryption is to protect the information that flows between peers on an unsecured network such as Internet. [3] | ||
| + | </ul> | ||
| + | </ul> | ||
| + | |||
| + | |||
| + | ==Applications== | ||
| + | An important goal in peer-to-peer networks is that all clients provide resources, including bandwidth, storage space, and computing power. Thus, as nodes arrive and demand on the system increases, the total capacity of the system also increases. [2] | ||
| + | |||
| + | |||
| + | ===General Usage=== | ||
| + | Peer-to-peer can be used for: | ||
| + | <ul> | ||
| + | *[http://en.wikipedia.org/wiki/File_sharing File sharing] - Files are stored and served by personal computers of the users. | ||
| + | |||
| + | *[http://en.wikipedia.org/wiki/VoIP VoIP] - A protocol optimized for the transmission of voice through the Internet or other packet switched networks. | ||
| + | |||
| + | *[http://en.wikipedia.org/wiki/Telephony Telephony] - Provide voice communication over distances, specifically by connecting telephones to each other. | ||
| + | |||
| + | *[http://en.wikipedia.org/wiki/Streaming_media Streaming media] - A kind of multimedia that is constantly received by, and normally displayed to, the end-user while it is being delivered by the provider. | ||
| + | |||
| + | *Software publication and distribution - Giving out a big software product with P2P networks and therefore peer can get the latest updated of the software. | ||
| + | |||
| + | *[http://en.wikipedia.org/wiki/Instant_Messaging Instant Messaging] - A real-time communication tool between two or more people based on typed text. | ||
| + | </ul> | ||
| + | |||
| + | |||
| + | ===Outside Computer Science=== | ||
| + | Peer-to-peer networks have also begun to attract attention outside computer science point of view, especially those deal with large data-sets. [2] | ||
| + | |||
| + | <ul> | ||
| + | *[http://en.wikipedia.org/wiki/Bioinformatics Bioinformatics] - P2P networks can used to run large programs designed to carry out tests to identify drug candidates. A program called [http://www.proteomecommons.org/dev/dfs/ Tranche] was developed to solve the bioinformatics data sharing problem in a secure and scalable fashion. [2] | ||
| + | |||
| + | *'''Education and Academia''' - Because P2P networks have fast distribution and large storage space features, many organizations are trying to apply it for educational and academic purposes. [2] | ||
| + | |||
| + | *'''Military''' - The U.S. Department of Defense has already started research on P2P networks as part of its modern network warfare strategy. However, due to security reasons, details are kept classified. [2] | ||
| + | |||
| + | *'''Business''' - It is still in the beginning states of using P2P networks in business areas. There are several reasons why companies prefer P2P networks, such as: Real-time collaboration, a process which requires strong computing power, etc. | ||
| + | </ul> | ||
| + | |||
| + | |||
| + | ==References== | ||
| + | [1] Declan, Jarlath, Keith, John, Dan, ''P2P Security'', TCD 4BA2 Project 2002/03, http://ntrg.cs.tcd.ie/undergrad/4ba2.02-03/p10.html | ||
| + | |||
| + | [2]''Peer-to-peer'', March 2008, http://en.wikipedia.org/wiki/Peer-to-peer | ||
| + | |||
| + | [3]Todd Sundsted, ''The practice of peer-to-peer computing: Trust and security in peer-to-peer networks'', 19 Jun 2002, http://www.ibm.com/developerworks/java/library/j-p2ptrust/ | ||
| + | |||
| + | [4] Tony Bradley, ''Peer-to-Peer (P2P) Network Security'', Four Steps To Sharing and Swapping Files Without Becoming a Victim, About.com, http://netsecurity.about.com/od/newsandeditorial1/a/p2psecurity.htm | ||
| + | |||
| + | [5]''PEER-TO-PEER SECURITY: The Dangers of P2P'', Websense, Inc., http://www.websense.com/global/en/ResourceCenter/p2p_security.php | ||
| + | |||
| + | [6]''Those aren’t just files you’re swapping – the dangers of Peer-to-Peer File Sharing'', Websense, Inc., Thttp://www.websense.com/docs/WhitePapers/PeertoPeer.pdf | ||
| + | |||
| + | [7]Vangie 'Aurora' Beal, ''All About Peer-To-Peer Architecture'', May 20, 2005, http://www.webopedia.com/DidYouKnow/Internet/2005/peer_to_peer.asp | ||
| + | |||
| + | |||
| + | ==See Also== | ||
| + | [[Streaming Media Technology]] | ||
| + | |||
| + | |||
| + | ==External Links== | ||
| + | *[http://www.ibm.com/developerworks/java/library/j-p2ptrust/ The practice of peer-to-peer computing: Trust and security in peer-to-peer networks] | ||
| + | *[http://ntrg.cs.tcd.ie/undergrad/4ba2.02-03/p10.html P2P Security] | ||
| + | |||
| + | |||
| + | |||
| + | --[[User:Chowkw|Chowkw]] 17:29, 8 April 2008 (EDT) | ||
Current revision as of 21:29, 8 April 2008
Peer-to-Peer (or P2P) networking is a fairly popular networking concept. Networks software such as BitTorrent and eMule make it easy for people to find what they want and share what they have. The first idea for using P2P networks are to exchange pirated audio, video, software, and other inappropriate content. An important thing should be noticed that share thing files on your computer with anonymous and unknown users on the public Internet could be dangerous and lead to security problem. [4,5]
Contents |
What is Peer to Peer Network
A pure peer-to-peer network does not have the notion of clients or servers, but only equal peer nodes that simultaneously function as both "clients" and "servers" to the other nodes on the network. An example for a non P2P file transfer is an FTP server where the client and server programs are quite distinct. P2P networks are generally simpler but they usually do not offer the same performance under heavy loads. The P2P network itself relies on computing power at the ends of a connection rather than from within the network itself. Besides file sharing, P2P networks are also used for Distributed Computation or Instant messaging. [2,7]
Network Structure
Peer-to-peer file sharing networks are transient Internet networks that allow computer users within the same P2P networking program to connect with each other computers and use sophisticated searching techniques to directly access and download files from one another's hard drives. The P2P overlay network consists of all the participating peers as network nodes. There are links between any two nodes that know each other. Based on how nodes link to each other, P2P networks can classify as Unstructured and Structured. [6,2]
Unstructured P2P networks
An unstructured P2P network is formed when the overlay links are established arbitrarily. Such networks can be easily constructed as a new peer that wants to join the network can copy existing links of another node and then form its own links over time. In an unstructured P2P network, if a peer wants to find a desired piece of data in the network, the query has to be flooded through the network to find as many peers as possible that share the data. The main disadvantage with such networks is that the queries may not always be resolved. Popular content is likely to be available at several peers and any peer searching for it is likely to find the same thing, but if a peer is looking for rare data shared by only a few other peers, then it is highly unlikely that search will be successful. [2]
Structured P2P networks
Structured P2P network employ a globally consistent protocol to ensure that any node can efficiently route a search to some peer that has the desired file, even if the file is extremely rare. Such a guarantee necessitates a more structured pattern of overlay links. By far the most common type of structured P2P network is the distributed hash table (DHT), in which a variant of consistent hashing is used to assign ownership of each file to a particular peer, in a way analogous to a traditional hash table's assignment of each key to a particular array slot. [2]
Security Concern
One major concern of using P2P architecture in the workplace is, of course, network security. Security concerns stem from the architecture itself. Today we find most blocking and routing handles by a specific server within network, but the P2P architecture has no single fixed server responsible for routing and requests. There are many kind of P2P networking attacks that cause the security problem and we have some example below. On the other hand, most of the security mechanisms using today are based on secret key, public key or combination of them. below has some introduction of the basic aspects of them. [7,1]
The picture below shows the weakness of security when using P2P applications. It shows that these applications are allow to go though the network and the network is now not secure. [1]
Attacks
- TCP port - To share files on the computer within a P2P network such as BitTorrent, a specific TCP port must be opened for the P2P software to communicate. In effect, once you open the port you are no longer protected from malicious traffic coming through it. [4]
- Trojans, Viruses - When files are downloading from other peer, there are no guarantee that the files being transfered are the one that you want. Also, when you double-click the EXE file, you can not sure that it has not installed a Trojans or bring viruses to the computer. [4]
- Bandwidth Clogging and File Sharing - P2P applications such as BitTorrent make it possible for one computer to share files with another computer located somewhere else on the Internet. A major problem with P2P file-sharing programs is that they result in heavy traffic, which clogs the institution networks. The rich audio and video files that P2P users share are very big. This affects response times for internal users as well as e-business customers and that results in lost income. [1]
Security Mechanisms
- Secret Key - Secret key techniques are based on the fact that the sender and recipient share a secret, which is used for various cryptographic operations, such as encryption and decryption of messages and the creation and verification of message authentication data. This secret key must be exchanged in a separate out of bound procedure prior to the intended communication (using a PKI for example). [1]
- Public Key - Public Key Techniques are based on the use of asymmetric key pairs. Usually each user is in possession of just one key pair. One of the pair is made publicly available, while the other is kept private. Because one is available there is no need for an out of band key exchange, however there is a need for an infrastructure to distribute the public key authentically. Because there is no need for pre-shared secrets prior to a communication, public key techniques are ideal for supporting security between previously unknown parties. [1]
- Trust - Trust is necessary in any distributed application -- P2P applications included. Trust can become a serious issue for P2P applications that distribute processing work to distributed computing nodes and then collect the results. If you trust a node within the network, you might be tempted to trust the content it provides. In some cases, this assumption is reasonable, but not always. Trust can established by these three standard elements. [3]
- Authentication - This process determine which node is in fact who or what that node declares itself to be. [3]
- Authorization - It gives an authentication to other node to access some subset of the resource s on another peer. [3]
- Encryption - This process coverts understandable information (plaintext) into a form difficult to understand by unauthorized individuals and systems. One use of encryption is to protect the information that flows between peers on an unsecured network such as Internet. [3]
Applications
An important goal in peer-to-peer networks is that all clients provide resources, including bandwidth, storage space, and computing power. Thus, as nodes arrive and demand on the system increases, the total capacity of the system also increases. [2]
General Usage
Peer-to-peer can be used for:
- File sharing - Files are stored and served by personal computers of the users.
- VoIP - A protocol optimized for the transmission of voice through the Internet or other packet switched networks.
- Telephony - Provide voice communication over distances, specifically by connecting telephones to each other.
- Streaming media - A kind of multimedia that is constantly received by, and normally displayed to, the end-user while it is being delivered by the provider.
- Software publication and distribution - Giving out a big software product with P2P networks and therefore peer can get the latest updated of the software.
- Instant Messaging - A real-time communication tool between two or more people based on typed text.
Outside Computer Science
Peer-to-peer networks have also begun to attract attention outside computer science point of view, especially those deal with large data-sets. [2]
- Bioinformatics - P2P networks can used to run large programs designed to carry out tests to identify drug candidates. A program called Tranche was developed to solve the bioinformatics data sharing problem in a secure and scalable fashion. [2]
- Education and Academia - Because P2P networks have fast distribution and large storage space features, many organizations are trying to apply it for educational and academic purposes. [2]
- Military - The U.S. Department of Defense has already started research on P2P networks as part of its modern network warfare strategy. However, due to security reasons, details are kept classified. [2]
- Business - It is still in the beginning states of using P2P networks in business areas. There are several reasons why companies prefer P2P networks, such as: Real-time collaboration, a process which requires strong computing power, etc.
References
[1] Declan, Jarlath, Keith, John, Dan, P2P Security, TCD 4BA2 Project 2002/03, http://ntrg.cs.tcd.ie/undergrad/4ba2.02-03/p10.html
[2]Peer-to-peer, March 2008, http://en.wikipedia.org/wiki/Peer-to-peer
[3]Todd Sundsted, The practice of peer-to-peer computing: Trust and security in peer-to-peer networks, 19 Jun 2002, http://www.ibm.com/developerworks/java/library/j-p2ptrust/
[4] Tony Bradley, Peer-to-Peer (P2P) Network Security, Four Steps To Sharing and Swapping Files Without Becoming a Victim, About.com, http://netsecurity.about.com/od/newsandeditorial1/a/p2psecurity.htm
[5]PEER-TO-PEER SECURITY: The Dangers of P2P, Websense, Inc., http://www.websense.com/global/en/ResourceCenter/p2p_security.php
[6]Those aren’t just files you’re swapping – the dangers of Peer-to-Peer File Sharing, Websense, Inc., Thttp://www.websense.com/docs/WhitePapers/PeertoPeer.pdf
[7]Vangie 'Aurora' Beal, All About Peer-To-Peer Architecture, May 20, 2005, http://www.webopedia.com/DidYouKnow/Internet/2005/peer_to_peer.asp
See Also
External Links
--Chowkw 17:29, 8 April 2008 (EDT)