Keystroke Logging
From Computing and Software Wiki
| Line 10: | Line 10: | ||
==History== | ==History== | ||
| - | [[ | + | [[www.google.ca|my text]], electronic spying, remote-computer monitoring, viruses, horses, and of course, keystroke logging, are all various threats openly available to everyone who uses computers; from gurus to illiterates. The question now lies on how well a user is protected against threats and attacks from malicious users. Hackers all around the world usually tend to communicate through the internet. Many have come together and formed their own websites that provide information about the world from the hackers’ point of view. One such site is www.antionline.com, another www.attrition.org. Even a site such as this, one created by hackers, for hackers, has been hacked at some point. Ever since the site teamed up with law enforcement officials, the site has been an outreach to hacking. They have been breached by some means so many times that logs have actually been posted of attempted hacks and threats. |
That being said, this paper can continue on forever, discussing the many different types of risks and security threats we face online today. So the main focus will be on keystroke logging. Keystroke logging, also known as key logging, has been a steal-string concept used ever since computers were first invented, and is continually growing as technology advances. It can be used in both a negative and position aspect. For example, its idea can be useful in law enforcement, as it provides a way to unlock passwords and encryption keys. FBI officials have used the technique to gather evidence, such as the PGP case. In this example, the FBI needed a password in order to decrypt coded files that allegedly contained records of illegal gambling and loan-sharking operations. So FBI officials decided to break into the son of the illicit Philadelphia mob boss’s business, and put a program on his computer (or perhaps an electronic bug in his keyboard) to record all the keystrokes. This is just one example of a case in which key logging was used to promote a positive gain. | That being said, this paper can continue on forever, discussing the many different types of risks and security threats we face online today. So the main focus will be on keystroke logging. Keystroke logging, also known as key logging, has been a steal-string concept used ever since computers were first invented, and is continually growing as technology advances. It can be used in both a negative and position aspect. For example, its idea can be useful in law enforcement, as it provides a way to unlock passwords and encryption keys. FBI officials have used the technique to gather evidence, such as the PGP case. In this example, the FBI needed a password in order to decrypt coded files that allegedly contained records of illegal gambling and loan-sharking operations. So FBI officials decided to break into the son of the illicit Philadelphia mob boss’s business, and put a program on his computer (or perhaps an electronic bug in his keyboard) to record all the keystrokes. This is just one example of a case in which key logging was used to promote a positive gain. | ||
Revision as of 21:07, 12 April 2009
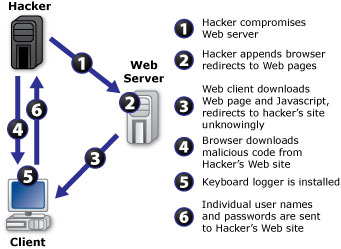
Keystroke logging commonly refers to the practice of logging (or storing) keystrokes, mouse events, and clipboard contents.
Most importantly, various login names, passwords, and other keystrokes can be recorded, in which important data such as credit card or banking information can be leaked out. The history of key logging is relative to the ease at which a computer can become infected; a user can simply visit the wrong website and become infected. Therefore, as users become more dependant on the accessibility of online networking, new security measures must be taken to accommodate for the risks involved with the convenience.
Keystroke loggers can be applied using three different methods: software, hardware, or kernel-driven applications. Information collected from key logging typically include host-names, IP addresses, and GUID (globally unique identifiers).
Contents |
History
my text, electronic spying, remote-computer monitoring, viruses, horses, and of course, keystroke logging, are all various threats openly available to everyone who uses computers; from gurus to illiterates. The question now lies on how well a user is protected against threats and attacks from malicious users. Hackers all around the world usually tend to communicate through the internet. Many have come together and formed their own websites that provide information about the world from the hackers’ point of view. One such site is www.antionline.com, another www.attrition.org. Even a site such as this, one created by hackers, for hackers, has been hacked at some point. Ever since the site teamed up with law enforcement officials, the site has been an outreach to hacking. They have been breached by some means so many times that logs have actually been posted of attempted hacks and threats. That being said, this paper can continue on forever, discussing the many different types of risks and security threats we face online today. So the main focus will be on keystroke logging. Keystroke logging, also known as key logging, has been a steal-string concept used ever since computers were first invented, and is continually growing as technology advances. It can be used in both a negative and position aspect. For example, its idea can be useful in law enforcement, as it provides a way to unlock passwords and encryption keys. FBI officials have used the technique to gather evidence, such as the PGP case. In this example, the FBI needed a password in order to decrypt coded files that allegedly contained records of illegal gambling and loan-sharking operations. So FBI officials decided to break into the son of the illicit Philadelphia mob boss’s business, and put a program on his computer (or perhaps an electronic bug in his keyboard) to record all the keystrokes. This is just one example of a case in which key logging was used to promote a positive gain.