Internet Control Message Protocol
From Computing and Software Wiki
| (27 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | The '''Internet Control Message Protocol''' ('''ICMP''') is mainly responsible for the sending of error messages to indicate issues that occur between networked entities on the internet. ICMP is a special-purpose message mechanism, and is considered a required part of the [[Internet Protocol]] (IP) which must be included in every IP implementation. Much like other network traffic, ICMP messages travel across the internet in the data portion of IP datagrams. The Internet Control Message Protocol can only report the error back to the original source of the datagram, it is the source's responsibility then to relate the error to a program or take other action to solve the problem. The major advantage of allowing hosts to use ICMP is that it provides a single mechanism for all control and information messages. Other than [[ping]] and [[traceroute]], ICMP is not usually used directly by user applications.<sup>[1]</sup> | + | The '''Internet Control Message Protocol''' ('''ICMP''') is mainly responsible for the sending of error messages to indicate issues that occur between networked entities on the [[internet]]. ICMP is a special-purpose message mechanism, and is considered a required part of the [[Internet Protocol]] (IP) which must be included in every IP implementation. Much like other network traffic, ICMP messages travel across the internet in the data portion of IP datagrams. The Internet Control Message Protocol can only report the error back to the original source of the datagram, it is the source's responsibility then to relate the error to a program or take other action to solve the problem. The major advantage of allowing hosts to use ICMP is that it provides a single mechanism for all control and information messages. Other than [[ping]] and [[traceroute]], ICMP is not usually used directly by user applications.<sup>[1]</sup> |
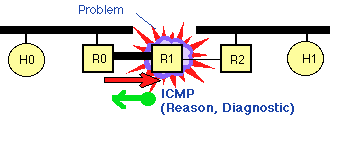
| + | [[Image:Icmp-gen.gif|thumb|right|400px|A datagram encounters a problem at R1 and an ICMP message is generated in response to this and sent back to the source of the original datagram<sup>[7]</sup>]] | ||
==Specification== | ==Specification== | ||
ICMP messages are created as a response to errors that may occur in IP datagrams or for routing or diagnostic purposes. The ICMP messages are generated at the IP layer, and is encapsulated and then transmitted much like IP datagrams. ICMP messages are generated in several situations, such as when a datagram cannot reach its destination or if the gateway does not have the buffering capacity to forward a datagram. These control messages are not considered reliable, as there is no guarantee that a datagram will be delivered. If reliability is required then higher level protocols which use IP must implement their own reliability procedures. ICMP messages are never sent in response to errors with ICMP messages themselves, as this could result in an infinite amount of messages. <sup>[2]</sup> | ICMP messages are created as a response to errors that may occur in IP datagrams or for routing or diagnostic purposes. The ICMP messages are generated at the IP layer, and is encapsulated and then transmitted much like IP datagrams. ICMP messages are generated in several situations, such as when a datagram cannot reach its destination or if the gateway does not have the buffering capacity to forward a datagram. These control messages are not considered reliable, as there is no guarantee that a datagram will be delivered. If reliability is required then higher level protocols which use IP must implement their own reliability procedures. ICMP messages are never sent in response to errors with ICMP messages themselves, as this could result in an infinite amount of messages. <sup>[2]</sup> | ||
===Format=== | ===Format=== | ||
| - | ICMP messages use the basic IP header and also an ICMP header. The ICMP header starts after bit 160 in the IP header and | + | ICMP messages use the basic IP header and also an ICMP header. The ICMP header starts after bit 160 in the IP header and can contain eight octets. The first octet of ICMP header is the ICMP type field, the value of which determines the format of the remaining data. This type can be further specified using the second octet, which contains the code. The value of the code determines what subtype the ICMP message is. For instance a message of type 3 code 1 is destination host unreachable, whereas a message of type 3 code 2 is destination protocol unreachable. Both of these messages are of the same main type, type 3, which is a destination unreachable message. The third and fourth octets of the ICMP header contain the checksum. The checksum field contains error checking data which is calculated from the ICMP header and data. The fifth and sixth octets contain the ID, which is returned in the case of an [[ping|Echo Reply]]. The seventh and eighth octets contain the sequence, which is also returned in the case of Echo Reply. If the ICMP message is not of the Echo Reply type, then the last four octets of the header are omitted in favour of other data. <sup>[2]</sup> |
| - | ===Partial List of | + | ===Partial List of Control Messages=== |
{|border="1" | {|border="1" | ||
! Type | ! Type | ||
| Line 59: | Line 60: | ||
| 3 || Redirect Datagram for the TOS & host | | 3 || Redirect Datagram for the TOS & host | ||
|- | |- | ||
| - | | 6 | + | | 6 - Alternate Host Address || ? || ? |
|- | |- | ||
| 7 || N/A || ''Reserved'' | | 7 || N/A || ''Reserved'' | ||
| Line 109: | Line 110: | ||
| 0 || Information Request | | 0 || Information Request | ||
|- | |- | ||
| - | | 31 | + | |rowspan=12| 31 - Datagram Conversion Error |
| + | | 0 || Unknown Error | ||
|- | |- | ||
| - | | | + | | 1 || Don't Convert Option Present |
|- | |- | ||
| - | | | + | | 2 || Unknown Mandatory Option Present |
|- | |- | ||
| - | | | + | | 3 || Known Unsupported Option Present |
|- | |- | ||
| - | | | + | | 4 || Unsupported Transport Protocol |
|- | |- | ||
| - | | | + | | 5 || Overall Length Exceeded |
|- | |- | ||
| - | | | + | | 6 || IP Header Length Exceeded |
|- | |- | ||
| - | | | + | | 7 || Transport Protocol > 255 |
|- | |- | ||
| - | | | + | | 8 || Port Conversion Out of Range |
|- | |- | ||
| - | | | + | | 9 || Transport Header Length Exceeded |
|- | |- | ||
| - | | | + | | 10 || 32-bit Rollover Missing and ACK set |
| + | |- | ||
| + | | 11 || Unknown Mandatory Transport Option Present | ||
| + | |- | ||
| + | | 32 - Mobile Host Redirect || ? || ? | ||
| + | |- | ||
| + | | 33 - Where-Are-You ([[The practicality of IPv6|IPv6]]) || ? || ? | ||
| + | |- | ||
| + | | 34 - Where-Are-You/Here-I-Am (IPv6) || ? || ? | ||
| + | |- | ||
| + | | 35 - Mobile Registration Request || ? || ? | ||
| + | |- | ||
| + | | 36 - Mobile Registration Reply || ? || ? | ||
| + | |- | ||
| + | | 37 - Domain Name Request || ? || ? | ||
| + | |- | ||
| + | | 38 - Domain Name Reply || ? || ? | ||
| + | |- | ||
| + | | 39 - SKIP Algorithm, Simple Key-Management || ? || ? | ||
| + | |- | ||
| + | |rowspan=6| 40 - Photuris, Security failures | ||
| + | | 0 || Bad SPI | ||
| + | |- | ||
| + | | 1 || Authentication Failed | ||
| + | |- | ||
| + | | 2 || Decompression Failed | ||
| + | |- | ||
| + | | 3 || Decryption Failed | ||
| + | |- | ||
| + | | 4 || Need Authentication | ||
| + | |- | ||
| + | | 5 || Need Authorization | ||
| + | |- | ||
| + | | 41 - ICMP for experimental mobility protocols || ? || ? | ||
|- | |- | ||
| 42 to 255|| N/A || ''Reserved'' | | 42 to 255|| N/A || ''Reserved'' | ||
|} | |} | ||
| - | <sup>[3],[4]</sup> | + | <sup>[3],[4],[5]</sup> |
| + | |||
| + | ==Utilization== | ||
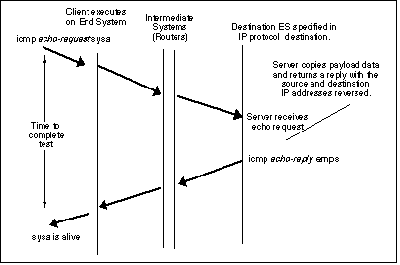
| + | ICMP can be an invaluable tool for network managers or users to identify network problems. For instance, a host or a router can send an ICMP echo request message to a specific location. Any machine which receives an echo request creates an echo reply and sends it back to the source of the request. So this request and reply can be used to determine whether a destination is reachable and responding. Since both the request and reply are sent in IP datagrams, successfully receiving the reply verifies that important parts of the transport system work.<sup>[1]</sup> | ||
| + | [[Image:Icmp-eg.gif|thumb|center|400px|Echo Request and Reply<sup>[7]</sup>]] | ||
| + | ===Misuses=== | ||
| + | While ICMP can be used to diagnose and repair a network, it can also be exploited in order to perform attacks. An example of this is the [[Denial Of Service Attacks|Denial of Service Attack]]. By clogging up a target machine with a large number of ICMP messages, or otherwise abusing how the network deals with these messages, an attacker can cause disruptions in service and maybe even a system crash.<sup>[6]</sup> | ||
== References == | == References == | ||
| Line 141: | Line 182: | ||
#Internet Control Message Protocol - DARPA Internet Program Protocol Specification. Retrieved on April 12th, 2009 from http://tools.ietf.org/html/rfc792 | #Internet Control Message Protocol - DARPA Internet Program Protocol Specification. Retrieved on April 12th, 2009 from http://tools.ietf.org/html/rfc792 | ||
#ICMP Type Numbers. Retrieved on April 12th, 2009 from http://www.iana.org/assignments/icmp-parameters. | #ICMP Type Numbers. Retrieved on April 12th, 2009 from http://www.iana.org/assignments/icmp-parameters. | ||
| - | # | + | #Internet Control Message Protocol. Retrieved on April 12th, 2009 from http://en.wikipedia.org/wiki/Internet_Control_Message_Protocol |
| + | #ICMP Packet Filtering. Retrieved on April 12th, 2009 from http://www.daemon.be/maarten/icmpfilter.html | ||
| + | #Types of DDoS attacks. Retrieved on April 12th, 2009 from http://anml.iu.edu/ddos/types.html#flood | ||
| + | #Internet Message Protocol (ICMP). Retrieved on April 12th, 2009 from http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/icmp.html | ||
== See also == | == See also == | ||
| Line 147: | Line 191: | ||
*[[Denial Of Service Attacks]] | *[[Denial Of Service Attacks]] | ||
*[[Smurfing]] | *[[Smurfing]] | ||
| + | *[[Ping]] | ||
| + | *[[Traceroute]] | ||
== External links == | == External links == | ||
| - | [http://tools.ietf.org/html/rfc792 | + | *[http://tools.ietf.org/html/rfc792 DARPA Internet Program Protocol Specification] |
| + | *[http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/icmp.html A Somewhat Illustrative Explanation] | ||
| + | *[http://en.wikipedia.org/wiki/Internet_control_message_protocol Wikipedia's Page on ICMP] | ||
--[[User:Collim|Collim]] 21:26, 4 April 2009 (EDT) | --[[User:Collim|Collim]] 21:26, 4 April 2009 (EDT) | ||
Current revision as of 02:27, 13 April 2009
The Internet Control Message Protocol (ICMP) is mainly responsible for the sending of error messages to indicate issues that occur between networked entities on the internet. ICMP is a special-purpose message mechanism, and is considered a required part of the Internet Protocol (IP) which must be included in every IP implementation. Much like other network traffic, ICMP messages travel across the internet in the data portion of IP datagrams. The Internet Control Message Protocol can only report the error back to the original source of the datagram, it is the source's responsibility then to relate the error to a program or take other action to solve the problem. The major advantage of allowing hosts to use ICMP is that it provides a single mechanism for all control and information messages. Other than ping and traceroute, ICMP is not usually used directly by user applications.[1]
Contents |
Specification
ICMP messages are created as a response to errors that may occur in IP datagrams or for routing or diagnostic purposes. The ICMP messages are generated at the IP layer, and is encapsulated and then transmitted much like IP datagrams. ICMP messages are generated in several situations, such as when a datagram cannot reach its destination or if the gateway does not have the buffering capacity to forward a datagram. These control messages are not considered reliable, as there is no guarantee that a datagram will be delivered. If reliability is required then higher level protocols which use IP must implement their own reliability procedures. ICMP messages are never sent in response to errors with ICMP messages themselves, as this could result in an infinite amount of messages. [2]
Format
ICMP messages use the basic IP header and also an ICMP header. The ICMP header starts after bit 160 in the IP header and can contain eight octets. The first octet of ICMP header is the ICMP type field, the value of which determines the format of the remaining data. This type can be further specified using the second octet, which contains the code. The value of the code determines what subtype the ICMP message is. For instance a message of type 3 code 1 is destination host unreachable, whereas a message of type 3 code 2 is destination protocol unreachable. Both of these messages are of the same main type, type 3, which is a destination unreachable message. The third and fourth octets of the ICMP header contain the checksum. The checksum field contains error checking data which is calculated from the ICMP header and data. The fifth and sixth octets contain the ID, which is returned in the case of an Echo Reply. The seventh and eighth octets contain the sequence, which is also returned in the case of Echo Reply. If the ICMP message is not of the Echo Reply type, then the last four octets of the header are omitted in favour of other data. [2]
Partial List of Control Messages
| Type | Code | Description |
|---|---|---|
| 0 - Echo Reply | 0 | Echo reply (used to ping) |
| 1 and 2 | N/A | Reserved |
| 3 - Destination Unreachable | 0 | Destination network unreachable |
| 1 | Destination host unreachable | |
| 2 | Destination protocol unreachable | |
| 3 | Destination port unreachable | |
| 4 | Fragmentation required, and DF flag set | |
| 5 | Source route failed | |
| 6 | Destination network unknown | |
| 7 | Destination host unknown | |
| 8 | Source host isolated | |
| 9 | Network administratively prohibited | |
| 10 | Host administratively prohibited | |
| 11 | Network unreachable for TOS | |
| 12 | Host unreachable for TOS | |
| 13 | Communication administratively prohibited | |
| 4 - Source Quench | 0 | Source quench (congestion control) |
| 5 - Redirect Message | 0 | Redirect Datagram for the Network |
| 1 | Redirect Datagram for the Host | |
| 2 | Redirect Datagram for the TOS & network | |
| 3 | Redirect Datagram for the TOS & host | |
| 6 - Alternate Host Address | ? | ? |
| 7 | N/A | Reserved |
| 8 - Echo Request | 0 | Echo request |
| 9 - Router Advertisement | 0 | Router Advertisement |
| 10 - Router Solicitation | 0 | Router discovery/selection/solicitation |
| 11 - Time Exceeded | 0 | TTL expired in transit |
| 1 | Fragment reassembly time exceeded | |
| 12 - Parameter Problem: Bad IP header | 0 | Pointer indicates the error |
| 1 | Missing a required option | |
| 2 | Bad length | |
| 13 - Timestamp | 0 | Timestamp |
| 14 - Timestamp Reply | 0 | Timestamp reply |
| 15 - Information Request | 0 | Information Request |
| 16 - Information Reply | 0 | Information Reply |
| 17 - Address Mask Request | 0 | Address Mask Request |
| 18 - Address Mask Reply | 0 | Address Mask Reply |
| 19 | N/A | Reserved for security |
| 20 to 29 | N/A | Reserved for robustness experiment |
| 30 - Traceroute | 0 | Information Request |
| 31 - Datagram Conversion Error | 0 | Unknown Error |
| 1 | Don't Convert Option Present | |
| 2 | Unknown Mandatory Option Present | |
| 3 | Known Unsupported Option Present | |
| 4 | Unsupported Transport Protocol | |
| 5 | Overall Length Exceeded | |
| 6 | IP Header Length Exceeded | |
| 7 | Transport Protocol > 255 | |
| 8 | Port Conversion Out of Range | |
| 9 | Transport Header Length Exceeded | |
| 10 | 32-bit Rollover Missing and ACK set | |
| 11 | Unknown Mandatory Transport Option Present | |
| 32 - Mobile Host Redirect | ? | ? |
| 33 - Where-Are-You (IPv6) | ? | ? |
| 34 - Where-Are-You/Here-I-Am (IPv6) | ? | ? |
| 35 - Mobile Registration Request | ? | ? |
| 36 - Mobile Registration Reply | ? | ? |
| 37 - Domain Name Request | ? | ? |
| 38 - Domain Name Reply | ? | ? |
| 39 - SKIP Algorithm, Simple Key-Management | ? | ? |
| 40 - Photuris, Security failures | 0 | Bad SPI |
| 1 | Authentication Failed | |
| 2 | Decompression Failed | |
| 3 | Decryption Failed | |
| 4 | Need Authentication | |
| 5 | Need Authorization | |
| 41 - ICMP for experimental mobility protocols | ? | ? |
| 42 to 255 | N/A | Reserved |
[3],[4],[5]
Utilization
ICMP can be an invaluable tool for network managers or users to identify network problems. For instance, a host or a router can send an ICMP echo request message to a specific location. Any machine which receives an echo request creates an echo reply and sends it back to the source of the request. So this request and reply can be used to determine whether a destination is reachable and responding. Since both the request and reply are sent in IP datagrams, successfully receiving the reply verifies that important parts of the transport system work.[1]
Misuses
While ICMP can be used to diagnose and repair a network, it can also be exploited in order to perform attacks. An example of this is the Denial of Service Attack. By clogging up a target machine with a large number of ICMP messages, or otherwise abusing how the network deals with these messages, an attacker can cause disruptions in service and maybe even a system crash.[6]
References
- Douglas E. Comer (2000). "Internetworking with TCP/IP Vol.1: Principles, Protocols, and Architecture". Internet Protocol: Error and Control Messages(ICMP) 129-145, Prentice Hall
- Internet Control Message Protocol - DARPA Internet Program Protocol Specification. Retrieved on April 12th, 2009 from http://tools.ietf.org/html/rfc792
- ICMP Type Numbers. Retrieved on April 12th, 2009 from http://www.iana.org/assignments/icmp-parameters.
- Internet Control Message Protocol. Retrieved on April 12th, 2009 from http://en.wikipedia.org/wiki/Internet_Control_Message_Protocol
- ICMP Packet Filtering. Retrieved on April 12th, 2009 from http://www.daemon.be/maarten/icmpfilter.html
- Types of DDoS attacks. Retrieved on April 12th, 2009 from http://anml.iu.edu/ddos/types.html#flood
- Internet Message Protocol (ICMP). Retrieved on April 12th, 2009 from http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/icmp.html
See also
External links
- DARPA Internet Program Protocol Specification
- A Somewhat Illustrative Explanation
- Wikipedia's Page on ICMP
--Collim 21:26, 4 April 2009 (EDT)