IP Spoofing
From Computing and Software Wiki
(Difference between revisions)
(New page: == IP Spoofing ==) |
|||
| Line 1: | Line 1: | ||
| - | == IP Spoofing == | + | '''IP(Internet Protocol) Spoofing''' is term used to describe the creation of IP Packets with a forged (spoofed) source IP address for the purposes of hiding the true identity of the sender or impersonating the identity of another system. IP Spoofing is generally used to gain unauthorized access to a network by impersonating a source with authorized access. IP Spoofing attacks are based on the fact that internet communication occurs between distant computers. The communication is handled by routers which decide the best path based on the destination address while the source address is generally ignored. Once the destination address has been reached, the destination machine reacts based on the source address. |
| + | |||
| + | == How IP Spoofing Works == | ||
| + | [[Image:Ipheader.jpg]] | ||
| + | |||
| + | IP Header | ||
| + | |||
| + | |||
| + | ==External links== | ||
| + | *[http://en.wikipedia.org/wiki/Spoofing_attack Wikipedia: Spoofing attack] | ||
| + | *[http://en.wikipedia.org/wiki/IP_spoofing Wikipedia: IP address spoofing] | ||
| + | *[http://www.securityfocus.com/infocus/1674 IP Spoofing: An Introduction] | ||
| + | *[http://www.giac.org/certified_professionals/practicals/gsec/0201.php Introduction to IP Spoofing] | ||
| + | *[http://www.cisco.com/web/about/ac123/ac147/archived_issues/ipj_10-4/104_ip-spoofing.html IP Spoofing, The Internet Protocol Journal, Volume 10, No. 4] | ||
Revision as of 23:23, 5 April 2009
IP(Internet Protocol) Spoofing is term used to describe the creation of IP Packets with a forged (spoofed) source IP address for the purposes of hiding the true identity of the sender or impersonating the identity of another system. IP Spoofing is generally used to gain unauthorized access to a network by impersonating a source with authorized access. IP Spoofing attacks are based on the fact that internet communication occurs between distant computers. The communication is handled by routers which decide the best path based on the destination address while the source address is generally ignored. Once the destination address has been reached, the destination machine reacts based on the source address.
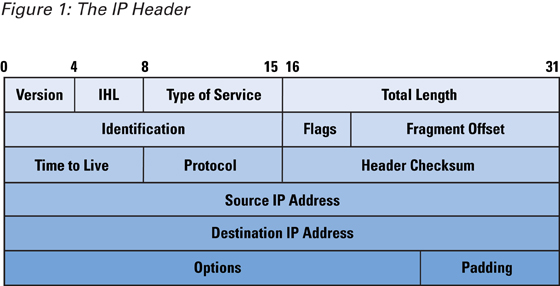
How IP Spoofing Works
IP Header