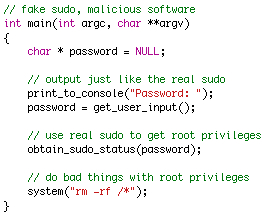
Malware
From Computing and Software Wiki
| Line 20: | Line 20: | ||
Sometimes malware authors create software that has no intended purpose what so ever. | Sometimes malware authors create software that has no intended purpose what so ever. | ||
| - | ==Types== | + | ==Types with examples== |
Typically malware is composed from a combination of several distinct types. | Typically malware is composed from a combination of several distinct types. | ||
=====Infectious===== | =====Infectious===== | ||
| - | * Viruses | + | Arguably the most common type, infectious malware is known for its self-replicating properties. |
| + | * Viruses | ||
| + | * Worms | ||
=====Hidden===== | =====Hidden===== | ||
| + | Hidden malware's key feature is its ability to hide itself in a computer system. | ||
* Trojan horses | * Trojan horses | ||
| + | * Root kits | ||
=====Deceptive===== | =====Deceptive===== | ||
| - | * Adware | + | The most bothersome, deceptive malware preys on users who may not be as tech-savvy as others. |
| + | * Adware | ||
| + | * Spyware | ||
==Prevention== | ==Prevention== | ||
Revision as of 20:03, 11 April 2009
Malicious software (malware) encompasses a broad range of software typically designed to covertly operate and deceive users to hide its actual intended purpose. It can be used as a catch-all phrase for software that has been programmed for malicious purposes intentionally; software such as viruses, worms, spyware, and botnets. Its purpose can vary, but typically it is used to gather information, generate profit, cause harm or data loss, or it could have no real purpose at all.
Contents |
History
Before computers were accessible to the general public, malware was not an overwhelming threat. Starting sometime in the 1970's computers became somewhat more common, and as a direct result, so did malicious software. At this time, viruses started to appear on networks such as ARPANET, gaining popularity into the 1980's with the explosion of person computers. Early malware was typically less of a threat, created by programmers who were trying to prank other users, rather than the typical malware created for todays society.
Purpose
There are numerous reasons why malware is written.
Obtaining sensitive information
Malware can be used to gather sensitive information. With the recent expansion of mobile computing, malware authors are targeting mobile computers, such as smart phones, because of the amount of sensitive information contained within them.
Obtaining financial returns
Malware can be used to generate illicit revenues, usually by hijacking ad revenues or using previously mentioned sensitive information to the benefit of the malware user.
Cause harm or data loss
The most common use of all, malware can be used to cause damage to a computer system in one way or another.
No real purpose
Sometimes malware authors create software that has no intended purpose what so ever.
Types with examples
Typically malware is composed from a combination of several distinct types.
Infectious
Arguably the most common type, infectious malware is known for its self-replicating properties.
- Viruses
- Worms
Hidden
Hidden malware's key feature is its ability to hide itself in a computer system.
- Trojan horses
- Root kits
Deceptive
The most bothersome, deceptive malware preys on users who may not be as tech-savvy as others.
- Adware
- Spyware
Prevention
- Linux lol