Proxy Server
From Computing and Software Wiki
| Line 35: | Line 35: | ||
== External Links == | == External Links == | ||
| - | + | [http://www.how-to-hide-ip.info/2008/01/24/risk-of-using-a-proxy-siteserver/ Safe Proxy Tools] | |
Revision as of 15:39, 11 March 2009
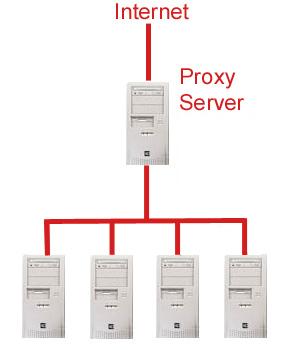
A proxy server is a server that acts as a liaison between a client seeking resources and a server that can provide that resource. The client makes a request to the proxy, which then evaulates the request according to its pre-set filtering rules. If the request is validated, the proxy makes the request of the target server on behalf of the client and provides the resource to the client. Sometimes the proxy server may modify the client's request or the server's response based on the filtering rules, and may even contact a server different than the specified one in order to provide the requested resource. Proxies are used to ensure security, administrative control and caching services.
Contents |
Functionality
A proxy server receives a request for a service (such as a Web page request) from a client. If it passes filtering requirements, the proxy server generally looks in its local cache of previously downloaded Web pages. If the page is found for example, the proxy returns it to the client without forwarding the request to the destination server. Otherwise, the proxy server acts as a client on behalf of the user and uses one of its own IP addresses to request the page from the server out on the Internet. When the page is returned, the proxy server relates it to the original request and forwards it on to the user.
To a user the proxy server is essentially non-existent; all Internet requests and returned responses appear to be directly with the addressed server. It should be noted however that the proxy is not necessarily invisible; its IP address has to be specified within the configuration options of the protocol program. <ref>"IP address has to be specified as a configuration option to the browser." WhatIs.com: http://whatis.techtarget.com/definition/0,,sid9_gci212840,00.html</ref>
An advantage of proxy servers is that all clients can theoretically access its cache. If one or more websites are frequently requested, these are likely to remain in the cache and improve response time. In fact, there are special proxy servers called cache servers. To this end, a proxy can also do logging. In addition, a proxy server can be separate or in the same machine as a firewall server and maintain the same functionality.
Types of Proxy Servers
There are many types of proxy servers that can act in different ways and provide similar but different functionality.
Caching
Web
Content-Filtering
Risks of Using a Proxy Server
Although proxy servers are perfectly legal, there are other dangers that you leave yourself vulnerable to when using a proxy.
Data Interception
Because proxy servers intercept data, there’s always the risk of the administrators of that proxy site to steal your information, such as account details to a website, personal identification like phone numbers, house address, or even your social security number (SSN) and credit card numbers. This is why it is very important for you to safeguard your information when using a proxy site by taking every possible measure to keep your identity a secret.
Be sure to check the proxy site for a Terms of Service link or a Privacy Policy so you know exactly what you’re getting yourself into. Sometimes, the proxy site will hide valuable information like that so you will just use their service without thinking about it. Even if they don’t, how many of us really read the terms of service and all that? Very few. So be sure to protect your information by looking through the site very carefully before you use it to enter any sensitive data into a form.
Also, if the website is not known and trusted or appear to have a good integrity, do not use it. This would only prove to endanger your information instead of finding a good proxy site to use. Keep this in mind before you use a proxy server next time or perhaps, your first time at all.
References
Template loop detected: Template:Reflist