Conventional Encryption Algorithms
From Computing and Software Wiki
(→Popular Algorithms) |
(→Popular Algorithms) |
||
| Line 43: | Line 43: | ||
|+ ''Conventional Encryption'' | |+ ''Conventional Encryption'' | ||
|- style="background:lightgray" | |- style="background:lightgray" | ||
| - | ! style="width:20% | + | ! style="width:20%" | Algorithm |
! style="width:20%" | Type | ! style="width:20%" | Type | ||
! style="width:40%" | Description | ! style="width:40%" | Description | ||
| Line 52: | Line 52: | ||
|- | |- | ||
| [http://en.wikipedia.org/wiki/ROT13 ROT13] || Monoalphabetic || | | [http://en.wikipedia.org/wiki/ROT13 ROT13] || Monoalphabetic || | ||
| + | |- | ||
| + | | [http://en.wikipedia.org/wiki/Bacon%27s_cipher Bacon] || Steganographic || | ||
|} | |} | ||
Revision as of 23:33, 8 April 2008
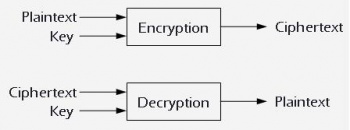
Conventional Encryption is ...
Contents |
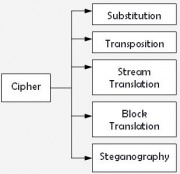
Classification of Ciphers
There are several techniques in which encryption algorithms can produce ciphertext. The simplest forms of encryption are via substitution, where plaintext symbols are replaced and via transposition, where plaintext symbols are rearranged. Other approaches such as stream and block translation involve converting plaintext to ciphertext either one symbol at a time or several symbols at a time respectively. In addition, steganographic techniques can be used, where symbols are introduced in the ciphertext to hide the plaintext meaning. A particular encryption/decryption implementation could incorporate multiple techniques to increase security.
Monoalphabetic
This is a substitution technique that uses a single alphabet to replace symbols of plaintext for symbols of ciphertext as dictated by the key. The key often represents the number of symbols to shift the plaintext from a circular alphabet. These techniques are relatively easy to break due to the fact that symbol frequencies remain invariant.
Polyalphabetic
This is a substitution technique that uses multiple alphabets to replace symbols of plaintext for symbols of ciphertext as dictated by the key. The key often represents a keyword where each letter defines the alphabet being used to encrypt each symbol of the plaintext. The keyword is repeated throughout the length of the message. These techniques suppress individual symbol frequency making these ciphers harder to break. However, the keyword length determines the periodicity in which alphabets are used. This periodicity is a major vulnerability of these types of ciphers.
Polygraphic
This is a substitution technique that replaces a group of n plaintext symbols by a group of n ciphertext symbols. In doing so, the individual frequency of symbols is hidden. In generality, this technique is similar to that of monoalphabetic ciphers with only using larger alphabets.
Route Transposition
This is a transposition technique where the plaintext is first written out in an mxn grid region. The key often represents a path on how to read from the grid, such as clockwise outward spiral, vertical zigzag, triangulation, etc. The ciphertext then becomes the sequence of symbols as read by the path. These techniques provide enormous amounts of available keys in which to use. However, some choices of keys are poor ones since they may leave sections of the ciphertext in their original or reversed plaintext order giving hints as to which key where used.
Columnar Transposition
This is a transposition technique where the plaintext is first written out in n-length rows. The key often represents a keyword of length n that defines the plaintext ordering of columns. The ordering could be done by sorting the keyword letters in alphabetical order or in any predefined order.
Synchronous Stream
This is a stream translation technique that combines plaintext with a key stream usually in the form of an XOR operation to form ciphertext one symbol at a time. These techniques require that the encoder and decoder be synchronized in the information they are processing. If information get introduced or lost during transition, decryption will be erroneous. If information gets corrupted only the particular symbol remains corrupted.
Asynchronous Stream
This is a stream translation technique that combines plaintext with a key stream that is generated from some fixed number of ciphertext symbols to produce the next ciphertext symbol.
Iterated Block
This is a block translation technique that iteratively converts an n-sized block of plaintext into ciphertext at the same time.
Fractioned Block
This is a block translation technique that breaks up single symbols into parts and then combines the pieces of multiple plaintext letters in order to get the ciphertext.
Steganographic
This is a technique that involves inserting random symbols at random locations of a plaintext message with the goal of hiding the message.
Popular Algorithms
| Algorithm | Type | Description |
|---|---|---|
| Rail Fence | Route Transposition | |
| ADFGVX | Fractionated Block | |
| ROT13 | Monoalphabetic | |
| Bacon | Steganographic |
References
[1] [2]
See Also
Public Key Encryption Algorithms
External Links
Elian April 8/2008