Transport Layer Security
From Computing and Software Wiki
(definition, history sections added) |
(finishing touches) |
||
| (13 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
| - | '''Transport Layer Security (TLS)''' is a cryptographic protocol that ensures privacy for communication over the Internet. It is the successor of the '''Secure Sockets Layer (SSL)''' protocol, though there are only minor differences that separate the two. | + | '''Transport Layer Security (TLS)''' is a cryptographic protocol that ensures privacy for communication over the Internet. It is the successor of the '''Secure Sockets Layer (SSL)''' protocol, though there are only minor differences that separate the two. TLS is composed of a handshake protocol and a record protocol. |
| - | + | ||
{| __TOC__ | {| __TOC__ | ||
|} | |} | ||
<br> | <br> | ||
| - | |||
==History== | ==History== | ||
| - | During the mid 1990s, it became obvious that security was necessary for Internet commerce. Many different mechanisms were proposed by different groups. Netscape, Inc. was the group that initially developed the protocol | + | During the mid 1990s, it became obvious that security was necessary for Internet commerce. Many different mechanisms were proposed by different groups. Netscape, Inc. was the group that initially developed the SSL protocol. While this was never formally adopted by the Internet Engineering Task Force (IETF), SSL was the basis of the IETF-designed protocol TLS which was first defined in 1999.[1] In fact, SSL and TLS are so similar that most implementations of SSL support TLS, and both protocols use the same port number. |
==How It Works== | ==How It Works== | ||
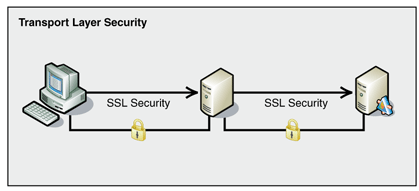
| + | [[Image:sslsecurity.gif|thumb|500px|right|'''Transport Layer Security'''<br>Multiple TLS/SSL connections must be opened if the message passes through several points. [2]]] | ||
| + | ===Handshake Protocol=== | ||
| + | TLS Handshake Protocol is used when the client wishes to open a secure connection to contact the server. The protocol allows each side to authenticate, so each side can be sure of whom they are communicating with. Both parties select the encryption algorithm to be used; it must be one that both sides support. TLS then allows the two sides to establish an encrypted connection. This is the highest level of security afforded, however many times only the server authenticates, and the client remains unauthenticated. This is less secure as the server cannot ensure that the client is who they claim to be, but this method is suitable under certain circumstances. [1] | ||
| + | If a message needs to go through multiple points to reach its destination, a new TLS connection must be opened for each intermediate point, as diagrammed at right. In this model, the message from the client is not protected cryptographically at each server due to the computationally expensive cryptographic operations that are performed for every new TLS connection that is established. [2] | ||
| - | == | + | ===Record Protocol=== |
| + | TLS Record Protocol uses the keys that are created in the Handshake Protocol to secure application data. It is also responsible for verifying its integrity and origin. For outgoing messages, the record protocol encrypts and divides these messages into manageable blocks, then compresses the blocks. Once encrypted, the outgoing data is passed to the Transmission Control Protocol (TCP) for transport. Likewise, for incoming messages, this protocol is responsible for decompressing the blocks, reassembling the incoming messages, and decryption. [3] | ||
| + | ==Applications== | ||
| + | TLS runs between application layers that run protocols like HTTP, FTP or SMTP, and layers that run transport protocols like TCP. TLS is most commonly run with the application protocol HTTP to form HTTPS. It can also be run with any other protocol that needs dependable connections. [4] | ||
| + | |||
| + | ==See Also== | ||
| + | * [[Transport_layer|Transport Layer]] | ||
| + | * [[Information_security_awareness|Information Security Awareness]] | ||
==References== | ==References== | ||
| - | + | * 1: Comer, Douglas E. (2006) "Internetworking with TCP/IP: Principles, Protocols, and Architecture, Fifth Edition" Upper Saddle River: Pearson Prentice Hall. ISBN 0-13-187671-6. | |
| + | * 2: "Chapter 3: Implementing Transport and Message Layer Security", Microsoft Developer Network, [http://msdn2.microsoft.com/en-us/library/aa480582.aspx http://msdn2.microsoft.com/en-us/library/aa480582.aspx] Retrieved on 2008-04-08. | ||
| + | * 3: "TLS Record Protocol", Microsoft Developer Network, [http://msdn2.microsoft.com/en-us/library/aa380514(VS.85).aspx http://msdn2.microsoft.com/en-us/library/aa380514(VS.85).aspx] Retrieved on 2008-04-08. | ||
| + | * 4: "Transport Layer Security", Wikipedia, [http://en.wikipedia.org/wiki/Transport_Layer_Security http://en.wikipedia.org/wiki/Transport_Layer_Security] Retrieved on 2008-04-08. | ||
==External Links== | ==External Links== | ||
| - | --[[User:Milesj2|Milesj2]] | + | * [http://msdn2.microsoft.com/en-us/library/aa480582.aspx Implementing Transport and Message Layer Security] |
| + | * [http://msdn2.microsoft.com/en-us/library/aa380514(VS.85).aspx TLS Record Protocol] | ||
| + | |||
| + | <br> | ||
| + | ---- | ||
| + | --[[User:Milesj2|Milesj2]] 22:39, 12 April 2008 (EDT) | ||
Current revision as of 02:39, 13 April 2008
Transport Layer Security (TLS) is a cryptographic protocol that ensures privacy for communication over the Internet. It is the successor of the Secure Sockets Layer (SSL) protocol, though there are only minor differences that separate the two. TLS is composed of a handshake protocol and a record protocol.
Contents |
History
During the mid 1990s, it became obvious that security was necessary for Internet commerce. Many different mechanisms were proposed by different groups. Netscape, Inc. was the group that initially developed the SSL protocol. While this was never formally adopted by the Internet Engineering Task Force (IETF), SSL was the basis of the IETF-designed protocol TLS which was first defined in 1999.[1] In fact, SSL and TLS are so similar that most implementations of SSL support TLS, and both protocols use the same port number.
How It Works
Handshake Protocol
TLS Handshake Protocol is used when the client wishes to open a secure connection to contact the server. The protocol allows each side to authenticate, so each side can be sure of whom they are communicating with. Both parties select the encryption algorithm to be used; it must be one that both sides support. TLS then allows the two sides to establish an encrypted connection. This is the highest level of security afforded, however many times only the server authenticates, and the client remains unauthenticated. This is less secure as the server cannot ensure that the client is who they claim to be, but this method is suitable under certain circumstances. [1]
If a message needs to go through multiple points to reach its destination, a new TLS connection must be opened for each intermediate point, as diagrammed at right. In this model, the message from the client is not protected cryptographically at each server due to the computationally expensive cryptographic operations that are performed for every new TLS connection that is established. [2]
Record Protocol
TLS Record Protocol uses the keys that are created in the Handshake Protocol to secure application data. It is also responsible for verifying its integrity and origin. For outgoing messages, the record protocol encrypts and divides these messages into manageable blocks, then compresses the blocks. Once encrypted, the outgoing data is passed to the Transmission Control Protocol (TCP) for transport. Likewise, for incoming messages, this protocol is responsible for decompressing the blocks, reassembling the incoming messages, and decryption. [3]
Applications
TLS runs between application layers that run protocols like HTTP, FTP or SMTP, and layers that run transport protocols like TCP. TLS is most commonly run with the application protocol HTTP to form HTTPS. It can also be run with any other protocol that needs dependable connections. [4]
See Also
References
- 1: Comer, Douglas E. (2006) "Internetworking with TCP/IP: Principles, Protocols, and Architecture, Fifth Edition" Upper Saddle River: Pearson Prentice Hall. ISBN 0-13-187671-6.
- 2: "Chapter 3: Implementing Transport and Message Layer Security", Microsoft Developer Network, http://msdn2.microsoft.com/en-us/library/aa480582.aspx Retrieved on 2008-04-08.
- 3: "TLS Record Protocol", Microsoft Developer Network, http://msdn2.microsoft.com/en-us/library/aa380514(VS.85).aspx Retrieved on 2008-04-08.
- 4: "Transport Layer Security", Wikipedia, http://en.wikipedia.org/wiki/Transport_Layer_Security Retrieved on 2008-04-08.
External Links
--Milesj2 22:39, 12 April 2008 (EDT)